Google XSS Example
21 Dec 2005Related: Google's XSS Vulnerability
In the comments to my previous blog post, Ivo Jansch asks:
To be able to comprehend how this may affect my website, could you explain how this could be exploited, even though you cannot demonstrate it?
Rather than offer another vague answer, I decided to provide a very simple proof of concept that demonstrates how character encoding inconsistencies can bite you. Google's vulnerability has of course been fixed, but with a simple PHP script, we can reproduce the situation:
<?phpheader('Content-Type: text/html; charset=UTF-7');$string = "<script>alert('XSS');</script>";$string = mb_convert_encoding($string, 'UTF-7');echo htmlentities($string);?>
If you run this PHP script, you should see a popup window:
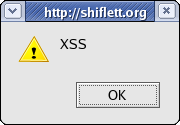
Although the output is escaped with htmlentities(), the JavaScript is still executed by the browser.
The example attack is a UTF-7 string (I just use mb_convert_encoding() for this demonstration), and the browser interprets the page as UTF-7 due to the Content-Type header. Internet Explorer makes this assumption automatically (thus, you can remove the explicit header() call), but this example should work in any browser.
Hopefully developers will begin to appreciate the necessity of character encoding consistency. If anyone ever tries to claim that it doesn't matter, you can point them here. :-)
